
Products
Software Platforms
Software Platforms
We are one of the very few leading high-end security solution providers which have our own dedicated in-house research and development laboratory, we are passionate about technological innovation and software design. Built with flexibility and security in mind, our range of professional software platforms can bring out the maximum capabilities of hardware system.

iPlatform Smart Security Management
- A powerful real-time security management platform for enterprise use
- Supports the latest biometric technologies including facial recognition and fingerprint verification
- Supports both industry standard and tailor-made applications, including Access Control, Attendance, POS, Lift Control, CCTV, e-Map, Alarm, Real-time Security Monitoring, Car Park, Service Subscription and third party applications
- Flexible and modularized design enabling an expanding network of access points
- Multiple time zones definition and grouping
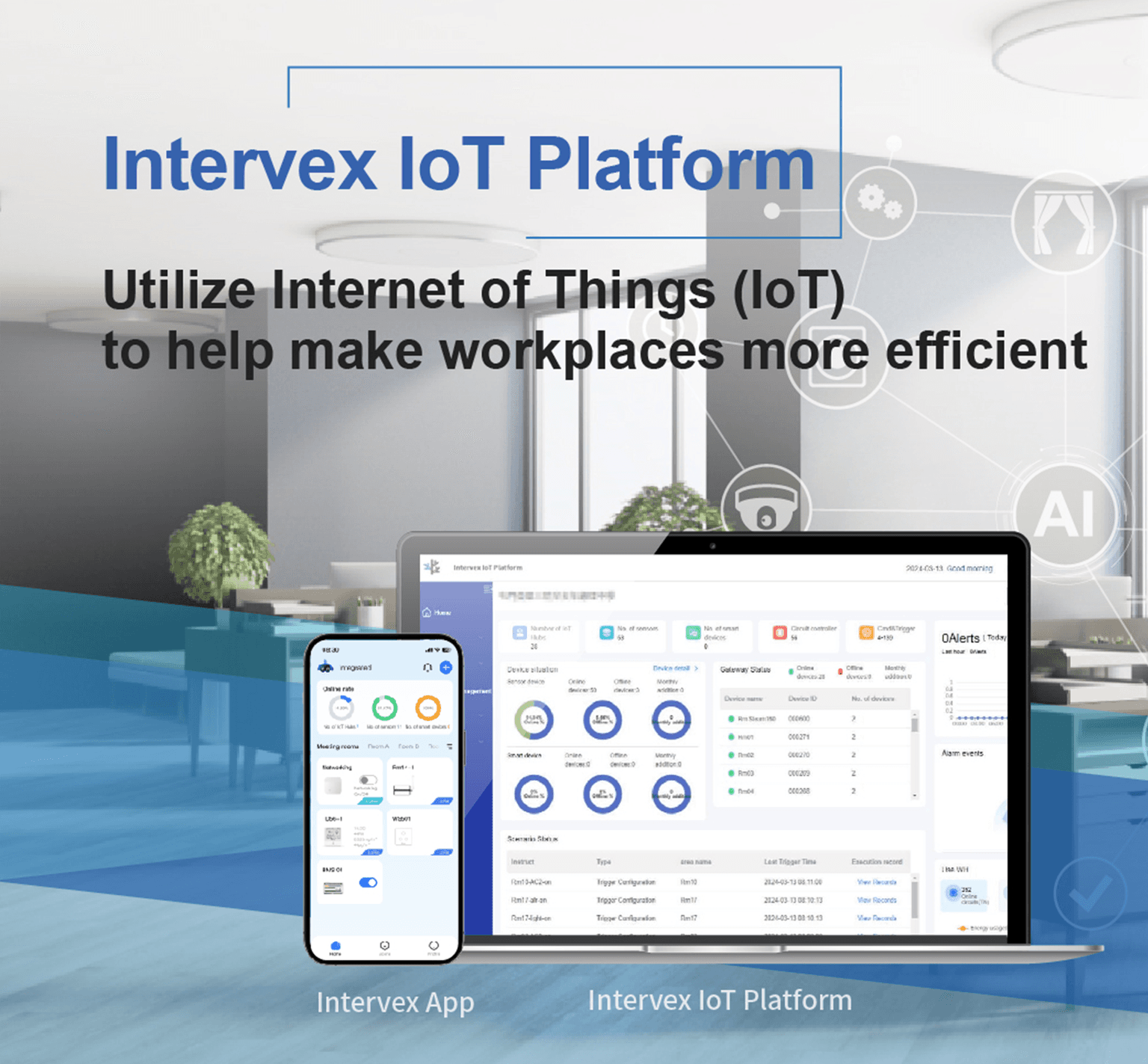
Intervex IoT Platform
- Powerful Device Management
- Smart IoT Alert
- Intelligent Sync
- Different kinds of scenarios
- Comprehensive security management platform

FaceX Face Recognition System
- Captures real-time faces for attendance
- Captures, compares and authorizes access
- Location tracking, time-zone setting, tracing on e-Map
- Customize VIP and blacklist face database
- Quick face registration

iScholar Smart Campus Management
- Real-time attendance reports for students and teachers at your finger tips
- Supports web browsers and Wechat instant notification
- Boost the confidence of students by praising good work and achievements
- Ensures the efficient allocation of school resources, simplifying school management

Java Embedded Security System (JESS)
- Point-to-point encryption in all data communication
- Mutual-authentication between server software, controllers and readers
- Utilizes Java EE n-Tier architecture to achieve enterprise-grade extensibility and scalability
- Real-time encrypted data upload (e.g. status, events and transactions)
- Unlimited shift table and roster table definitions