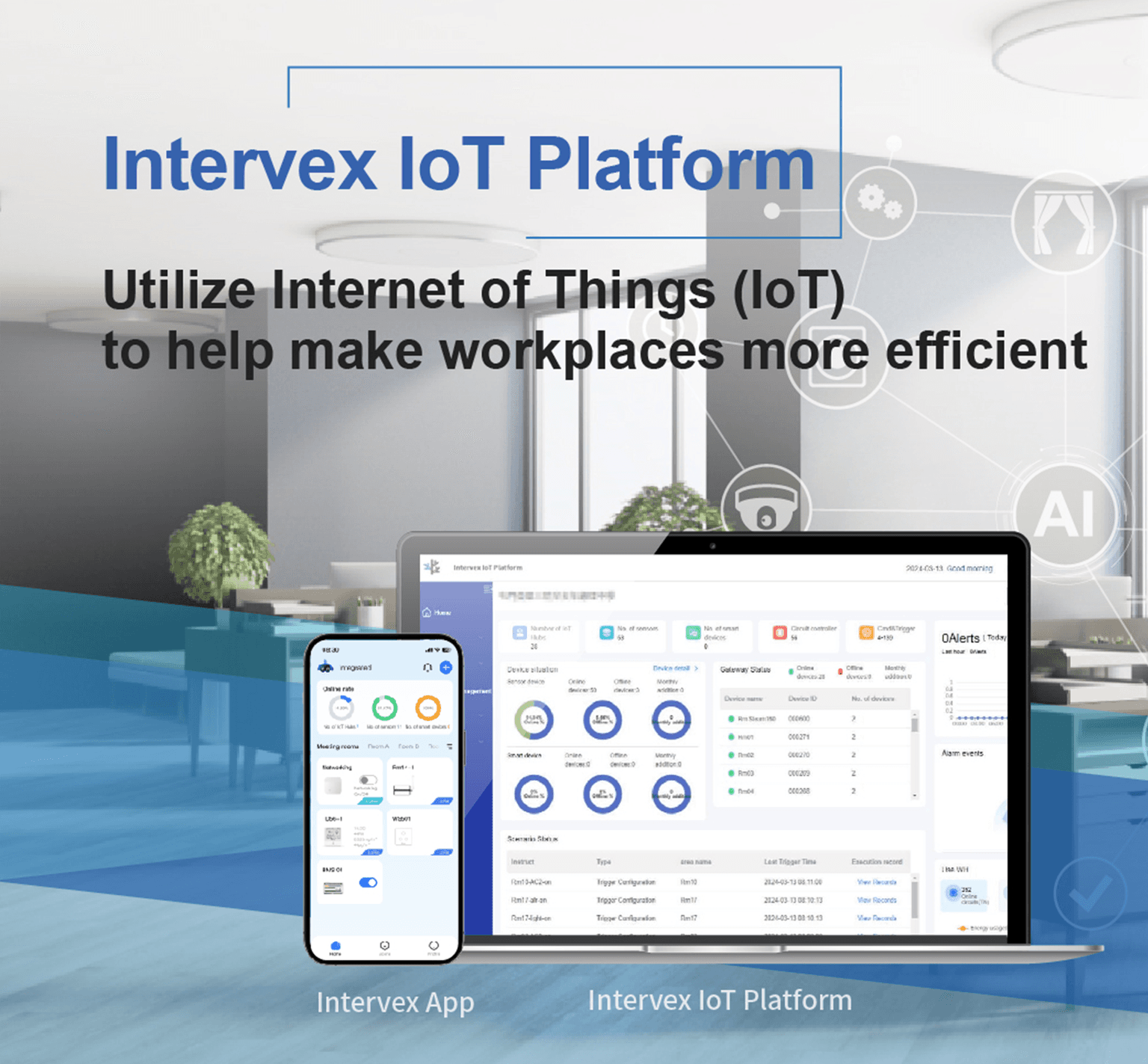
Intervex IoT Platform
Integrated’s Intervex IoT Platform seamlessly integrates cutting-edge IoT and AI technologies to redefine intelligent management standards for modern workspaces. By combining advanced security management with access control, it enables precise scheduling and utilization of shared office resources such as workstations and meeting rooms. Powered by robust IoT infrastructure, Intervex IoT allows users to monitor real-time environmental data and optimize energy consumption through a user-friendly mobile App or desktop interface.
Designed to meet the comprehensive needs of businesses, Intervex IoT addresses critical areas such as safety management, space optimization, environmental monitoring, and energy efficiency. It empowers organizations to create a smarter, more efficient, and sustainable office ecosystem, ensuring they stay ahead in the competitive business landscape. With Intervex IoT, your business gains the tools to lead with confidence and secure long-term success.
System Highlights
Powerful Device Management
Manage devices online and export statistical reports
Smart IoT Alert
Direct control of group authorization, alarm settings, real-time notification and intelligent power failure management all help to ensure user safety
Intelligent Sync
Monitor and control from anywhere. All devices are just one click away
Different kinds of scenarios
Reservation permissions, access control rights, lights, air-conditioning and other electrical devices can be controlled directly helping you achieve your safety and energy-saving objectives in one move
Comprehensive security management platform
Seamlessly compatible with the iPlatform security management platform to meet all your security requirements such as access control, attendance, POS, CCTV, etc








